The Convergence of Enterprise Architecture and Cybersecurity
The Convergence of Enterprise Architecture and Cybersecurity
Introduction
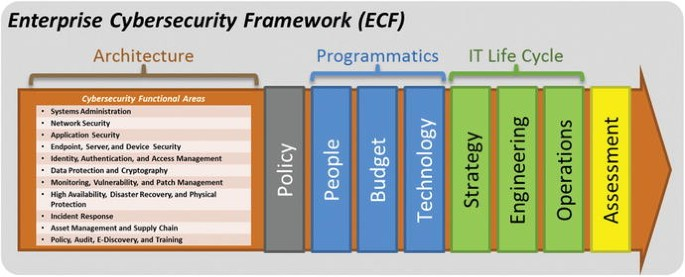
In today’s digital landscape, where organizations heavily rely on technology to drive their operations, the need for a robust and secure architecture has become paramount. As enterprises strive to stay ahead of the curve, they must address the interplay between Enterprise Architecture (EA) and cybersecurity. This article will delve into the convergence of EA and cybersecurity, highlighting best practices for creating a secure architecture that can withstand the ever-evolving threat landscape.
The Role of Enterprise Architecture
Enterprise Architecture serves as a blueprint for organizations, providing a holistic view of their structure, processes, and technology landscape. It enables businesses to align their IT capabilities with their strategic goals, optimize operations, and drive innovation. EA encompasses various domains, including business architecture, information architecture, application architecture, and technology architecture.
With a comprehensive EA framework, organizations gain several key benefits:
- Strategic alignment between business objectives and technology
- Improved coordination across business units and functions
- Enhanced agility and flexibility to respond to change
- Reduced IT costs through system consolidation and reuse
- Management of risk across the enterprise
According to Gartner, 75% of organizations engaged in digital transformation initiatives will leverage EA to guide their efforts by 2025.
The Growing Importance of Cybersecurity
As organizations become more digitally interconnected, the risk of cyber threats and data breaches increases exponentially. Cybersecurity is no longer an afterthought but a critical aspect of enterprise operations. It involves protecting sensitive data, systems, and networks from unauthorized access, disruption, and damage. A robust cybersecurity strategy is essential to safeguarding an organization’s reputation, customer trust, and overall business continuity.
Some key stats that highlight the growing importance of cybersecurity:
-
Cyber crime costs are expected to reach $10.5 trillion annually by 2025, up from $3 trillion in 2015 (Cybersecurity Ventures)
-
90% of companies experienced a data breach in the past two years (IBM)
-
Data breaches cost companies an average of $4.24 million per incident in 2021 (IBM)
-
Ransomware attacks increased by 105% in 2021 compared to 2020 (SonicWall)
The Interplay between EA and Cybersecurity
The convergence of EA and cybersecurity is crucial for creating a secure architecture that can withstand the dynamic threat landscape. By integrating cybersecurity principles into the EA framework, organizations can proactively identify and mitigate potential vulnerabilities. Here are some key areas where EA and cybersecurity intersect:
Risk Assessment and Management
Enterprise Architecture provides a comprehensive understanding of an organization’s assets, processes, and dependencies. By conducting a thorough risk assessment, organizations can identify potential security gaps and prioritize their mitigation efforts. This involves analyzing the impact and likelihood of various threats and vulnerabilities, considering both internal and external factors. The insights gained from the risk assessment can inform the development of a robust cybersecurity strategy.
Security by Design
Integrating cybersecurity into the design phase of the EA process ensures that security measures are built into the architecture from the ground up. This approach, known as “security by design,” emphasizes the proactive identification and mitigation of security risks. By considering security requirements early in the design process, organizations can avoid costly retrofits and reduce the overall attack surface.
Access Control and Identity Management
Effective access control and identity management are essential components of a secure architecture. Enterprise Architecture can help organizations define and enforce access control policies, ensuring that only authorized individuals have access to sensitive data and systems. This involves implementing robust authentication mechanisms, such as multi-factor authentication, and establishing clear roles and responsibilities for user access.
Incident Response and Recovery
In the event of a cybersecurity incident, organizations must have a well-defined incident response and recovery plan in place. Enterprise Architecture can facilitate this process by providing a clear understanding of the organization’s IT infrastructure and dependencies. By mapping out critical systems and data flows, organizations can quickly identify and contain security breaches, minimize the impact, and restore normal operations.
Continuous Monitoring and Improvement
Cybersecurity is an ongoing process that requires continuous monitoring and improvement. Enterprise Architecture can help organizations establish a framework for monitoring and evaluating the effectiveness of their security controls. By regularly assessing the architecture’s security posture, organizations can identify emerging threats, address vulnerabilities, and adapt their security measures accordingly.
Best Practices for a Secure Architecture

To ensure a secure architecture that effectively addresses the interplay between EA and cybersecurity, organizations should consider the following best practices:
-
Implement Defense-in-Depth: Adopt a layered approach to security, implementing multiple security controls at different levels to provide comprehensive protection against threats.
-
Stay Updated with Security Standards: Keep abreast of the latest security standards and frameworks, such as ISO 27001, NIST Cybersecurity Framework, and CIS Controls. Aligning with these standards can help organizations establish a strong security foundation.
-
Regularly Assess and Test Security Controls: Conduct regular security assessments and penetration testing to identify vulnerabilities and validate the effectiveness of security controls. This proactive approach can help organizations stay one step ahead of potential threats.
-
Educate and Train Employees: Invest in cybersecurity awareness and training programs to educate employees about the importance of security and their role in maintaining a secure architecture. Human error is often a significant factor in security breaches, so fostering a security-conscious culture is crucial.
-
Engage in Threat Intelligence Sharing: Collaborate with industry peers and security communities to share threat intelligence and stay informed about emerging threats. By leveraging collective knowledge, organizations can enhance their security posture and respond effectively to new challenges.
Frequently Asked Questions (FAQ)
Q1: How does Enterprise Architecture contribute to cybersecurity?
Enterprise Architecture provides a holistic view of an organization’s structure, processes, and technology landscape. By integrating cybersecurity principles into the EA framework, organizations can proactively identify and mitigate potential vulnerabilities, ensuring a secure architecture.
Q2: What is “security by design”?
“Security by design” is an approach that emphasizes integrating cybersecurity measures into the design phase of the Enterprise Architecture process. By considering security requirements early on, organizations can build security into the architecture from the ground up, reducing the risk of vulnerabilities and the need for costly retrofits.
Q3: How can access control and identity management be enforced in a secure architecture?
Access control and identity management can be enforced by implementing robust authentication mechanisms, such as multi-factor authentication, and defining clear roles and responsibilities for user access. Enterprise Architecture can help organizations establish and enforce access control policies to ensure that only authorized individuals have access to sensitive data and systems.
Q4: What is the importance of incident response and recovery in a secure architecture?
Incident response and recovery are crucial in a secure architecture to effectively handle cybersecurity incidents. Enterprise Architecture provides a clear understanding of an organization’s IT infrastructure and dependencies, enabling quick identification and containment of security breaches. A well-defined incident response and recovery plan minimizes the impact of incidents and helps restore normal operations.
Q5: How can organizations continuously improve their security measures?
Organizations can continuously improve their security measures by establishing a framework for monitoring and evaluating the effectiveness of their security controls. Enterprise Architecture can help in regularly assessing the architecture’s security posture, identifying emerging threats, addressing vulnerabilities, and adapting security measures accordingly. This proactive approach ensures that security measures are up to date and effective.
Conclusion
The convergence of Enterprise Architecture and cybersecurity is essential in today’s digital landscape. By integrating cybersecurity principles into the EA framework, organizations can create a secure architecture that effectively addresses the ever-evolving threat landscape. Implementing best practices, such as defense-in-depth, staying updated with security standards, regularly assessing security controls, educating employees, and engaging in threat intelligence sharing, will further enhance the security posture of organizations. With a strong and secure architecture, organizations can protect their assets, maintain customer trust, and ensure business continuity in the face of cybersecurity challenges.
Find more about our framework guide on Framework Docs
Find more about our conprehensive Enterprise Architecture Guide